
About AWS CloudTrail
CloudTrail provides a comprehensive event history of your AWS account activity, including actions taken through the AWS Management Console, AWS SDKs, command line tools, and other AWS services. This enables governance, compliance, operational auditing, and risk auditing of your AWS account.
Enabling CloudTrail
AWS CloudTrail is now enabled by default for ALL CUSTOMERS and will provide visibility into the past seven days of account activity without the need for you to configure a trail in the service to get started. If you want to access your CloudTrail log files directly or archive your logs for auditing purposes, you can still create a trail and specify the S3 bucket for your log file delivery. Creating a trail also allows you to deliver events to CloudWatch Logs and CloudWatch Events. Please follow the below steps:
Step 1: Go to your CloudTrail service console under the Services dropdown. 
Step 2: Click on Trails from the left navigation and then click onCreate trail. 
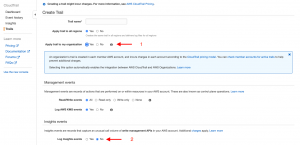
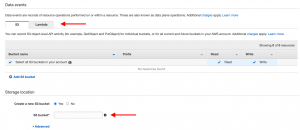
Step 3: Enter the trail name. You can enable features based on your requirements or stick to default will also serve your basic needs. Below are a few non-default features we enabled along with an explanation of our reasons. Next, select an existing S3 bucket or AWS will create a new bucket for you to save the logs. A) Apply trail to my organization: If you have multiple AWS accounts, this feature will help you get everything in one single place. B) Insights events: Insight events helps you track unusual call volumes of write management APIs. Say, your account keys are compromised and a hacker is trying to launch multiple instances. This type of write operation can be tracked by Insight. Do keep in mind that CloudTrail Insights events are charged at $0.35 per 100,000 write management events analyzed so you may end up paying a more than you expected. Please visit the pricing model page here to verify if you have the budget for this. C) Data events: Data events records resource operations performed on or within a resource, for S3 and lambda. E.g.: S3 GetObject, PutObject can be tracked based on individual buckets.
Pricing
In CloudTrail, you can view, filter and download the most recent 90 days of your account activity for all management events in supported AWS services, free of charge. Please refer to this page here for more on pricing details.






